The below is an excerpt from Best Practices for Social Media Archiving and Security from Osterman Research. The full report is available for download here.
Social media provides a number of benefits, but creates the opportunity for organizations to be exposed to a variety of cyber threats, as well as legal, regulatory and other problems.
1. ABSENCE OF SOCIAL MEDIA POLICIES IN MANY ORGANIZATIONS
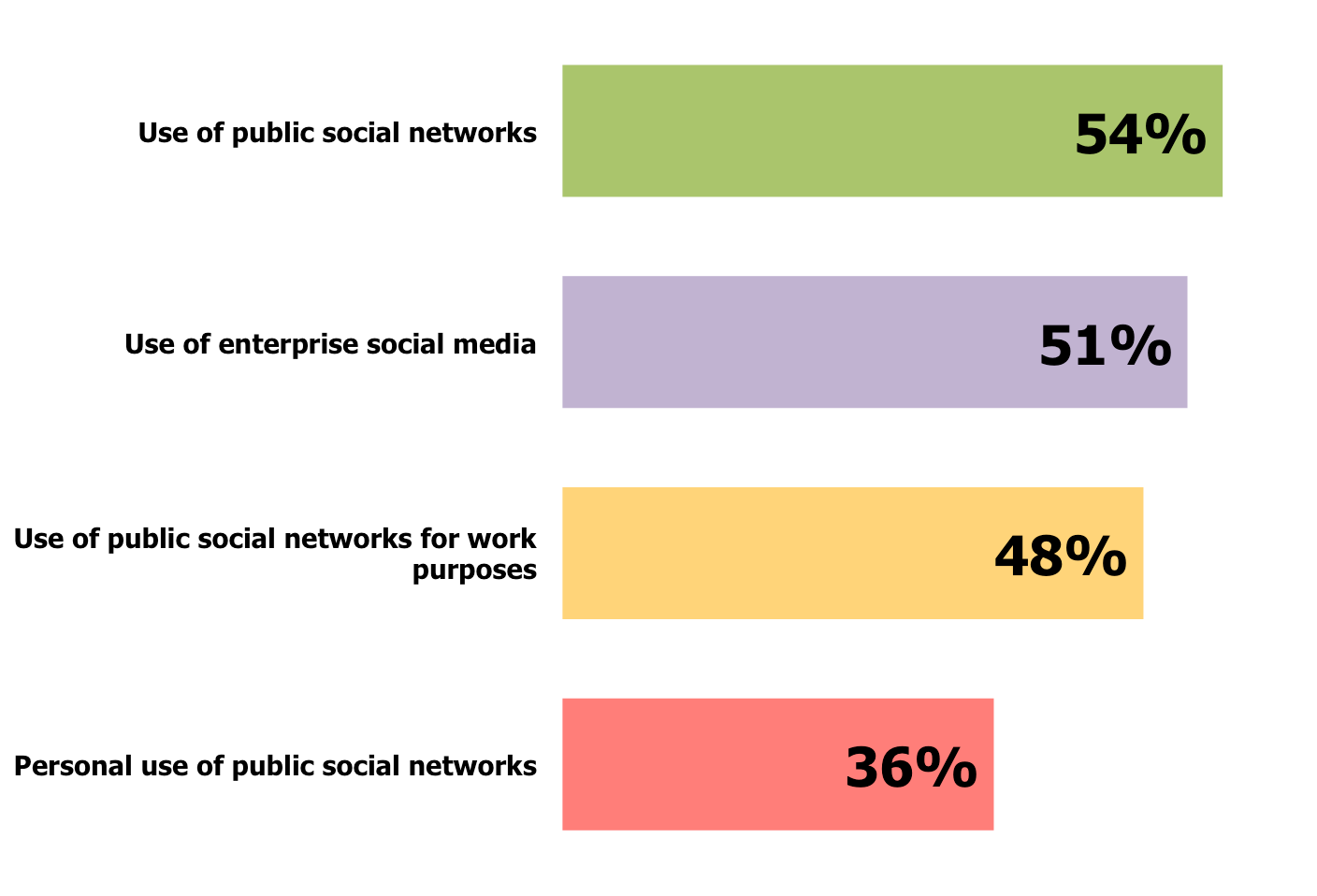
A large proportion of organizations do not have written policies about the use of various types of social media. For example, as shown in Figure 4, among organizations that have deployed enterprise social media, only 51% have written policies about its use and only 48% of these organizations have a policy about the use of public social networks when employed for work-related purposes.
Figure 4: Presence of a Written Policy About Various Types of Social Media Among Organizations That Have Deployed Enterprise Social Media
Osterman Research believes that all organizations should have a set of detailed and thorough social media policies that includes a number of things, including:
- Specification about the tools that are and are not permitted for use on the corporate network.
- Rules about whether or not employees can speak on behalf of the company and the extent to which they can do so.
- The types of content that can be shared via social media.
- To what extent personal accounts can be used for business purposes.
- Unambiguous details about who owns social media contacts, such as Twitter followers, if and when an employee leaves the company.
- Initial training of end users on these policies and continual training as policies are updated.
One danger that can occur in the absence of detailed and thorough social media policies is that data can accidentally be leaked through social media channels, resulting in a number of negative consequences. While a leak of information, such as sharing an embargoed announcement, can occur through social media, there are more subtle forms of leakage. For example, an employee who innocently tweets their travel plans might be divulging her company’s plan to enter a partnership with another company or to be acquired. Similarly, an employee who shares racially or sexually offensive jokes through social media can create problems with fellow employees, customers, business partners and others. To prevent these types of problems, social media policies should be very clear and prescriptive about employee obligations not to share any information that could harm other employees or the business itself.
2. CONTENT IS NOT PROPERLY ARCHIVED
Social media platforms – whether enterprise social solutions that have been deployed by an organization or consumer-focused, public systems – contain various types of business records that must be retained. However, our survey found that 66% of the organizations surveyed are not archiving content from external social networks, while 43% of organizations that have deployed an enterprise social platform are not doing so either. Many decision makers are simply not aware of their organizations’ legal or regulatory obligations to retain social media content, but this can result in serious problems. While the focus of social media management and control is today skewed heavily toward financial services, there is growing expansion into other heavily regulated industries, as well. Organizations that do not archive content from social media platforms face significant and growing risks from their inaction. For example:
- Our research found that 26% of organizations have had to produce content for eDiscovery from their enterprise social media platform. Osterman Research anticipates that this figure will grow dramatically over the next two years.
- There are a variety of regulatory obligations to retain business records generated by or stored in social media platforms. For example the Financial Industry Regulatory Authority (FINRA) Regulatory Notice 10-06, Regulatory Notice 11-39, and Rule 2210(c)(6); the Federal Financial Institutions Examination Council (FFIEC) Social Media Guidance; and the Financial Conduct Authority (FCA) GC14/6 all place requirements on regulated organizations to retain relevant social media content. A failure to comply with these obligations can be expensive and embarrassing. For example, a broker who defended a drug company’s stock in a Facebook post was fined and temporarily suspended for the post.
- Governments at various levels have open-records requirements and Freedom of Information Act (FOIA) obligations to retain and produce electronic records, which increasingly will include social media posts.
In addition to regulatory obligations to retain social media content, there is a growing body of court decisions that increasingly cite and/or require retention of social media content. Gibson Dunn, in its 2015 Mid-Year E-Discovery Update, reported that “….the number of cases focusing on the discovery of social media continued to skyrocket in the first half of 2015.” For example:
- In D.O.H. v. Lake Central School Corp., the plaintiff had deleted relevant information from his Facebook account and the court found that such deletion constituted spoliation of evidence.
- In Hannah v. Northeastern State University, two professors posted racist comments on Facebook about a department chair that was denied tenure. The chair sued the university, claiming a hostile work environment. The court found there to be a causal connection between the tenure issue and the plaintiff’s complaints about race discrimination.
- In Calvert v. Red Robin International, Inc.vi, the plaintiff was ordered by the court to “bring all materials, electronic or otherwise, including e-mails, Facebook messages, and any other communications he has had with putative class members in this action”.
- In Crowe v. Marquette Transportation, a US federal court ordered an employee to reactivate his Facebook account, produce a complete copy of his entire Facebook page, and allow his employer to review all of his Facebook messages.
In short, decision makers must realize that social media content is fundamentally no different than more traditional forms of electronic information, and so records contained within social media platforms – whether enterprise or consumer-focused – must be retained and producible for purposes of eDiscovery, litigation holds, regulatory compliance, or corporate best practice. Moreover, it is essential that employers monitor social media posts for egregious violations of corporate policy, the law and regulatory requirements.
3. DATA CAN BE BREACHED
Social media provides another avenue by which corporate data can be breached. For example:
- Loss of customer lists
- In Eagle v. Morgan, the court ruled that a LinkedIn profile, including all of its contacts, belongs to the employee if the employer has not established a social media policy specifically stating otherwise. This can result in a company’s loss of key business and other contacts to a competitor if an employee leaves. In a similar case, PhoneDog v. Kravitz, an employer lost control of a corporate Twitter account and its approximately 17,000 followers after an employee left the company.
- Revelation of trade secrets through geolocation
- Many social media platforms will allow users to indicate their location at the time of a post or will automatically do this for them. Use of geolocation by traveling employees or senior executives can inadvertently reveal confidential information about a merger, acquisition or some other arrangement. This is particularly true when location information makes it easy to infer the company one is visiting, such as Bentonville, AR (Walmart); Corning, NY (Corning, Inc.); Harrison, NY (Pepsico and MasterCard); or Deerfield, IL (Walgreens).
- Accidental release of confidential information
- In May 2012, Microsoft accidentally posted information about the availability of the Windows 8 Release Preview on a blog, which followed the accidental release of information about its social search network, which at the time was a confidential research project. In late 2014, the CFO of Twitter mistakenly sent a message about acquiring another company to his 9,000 followers – he had meant to send it as a direct message to one individual. In 2011, an HP vice president mistakenly revealed details about the company’s cloud-computing offerings via LinkedIn x.
4. AN INGRESS POINT FOR MALWARE
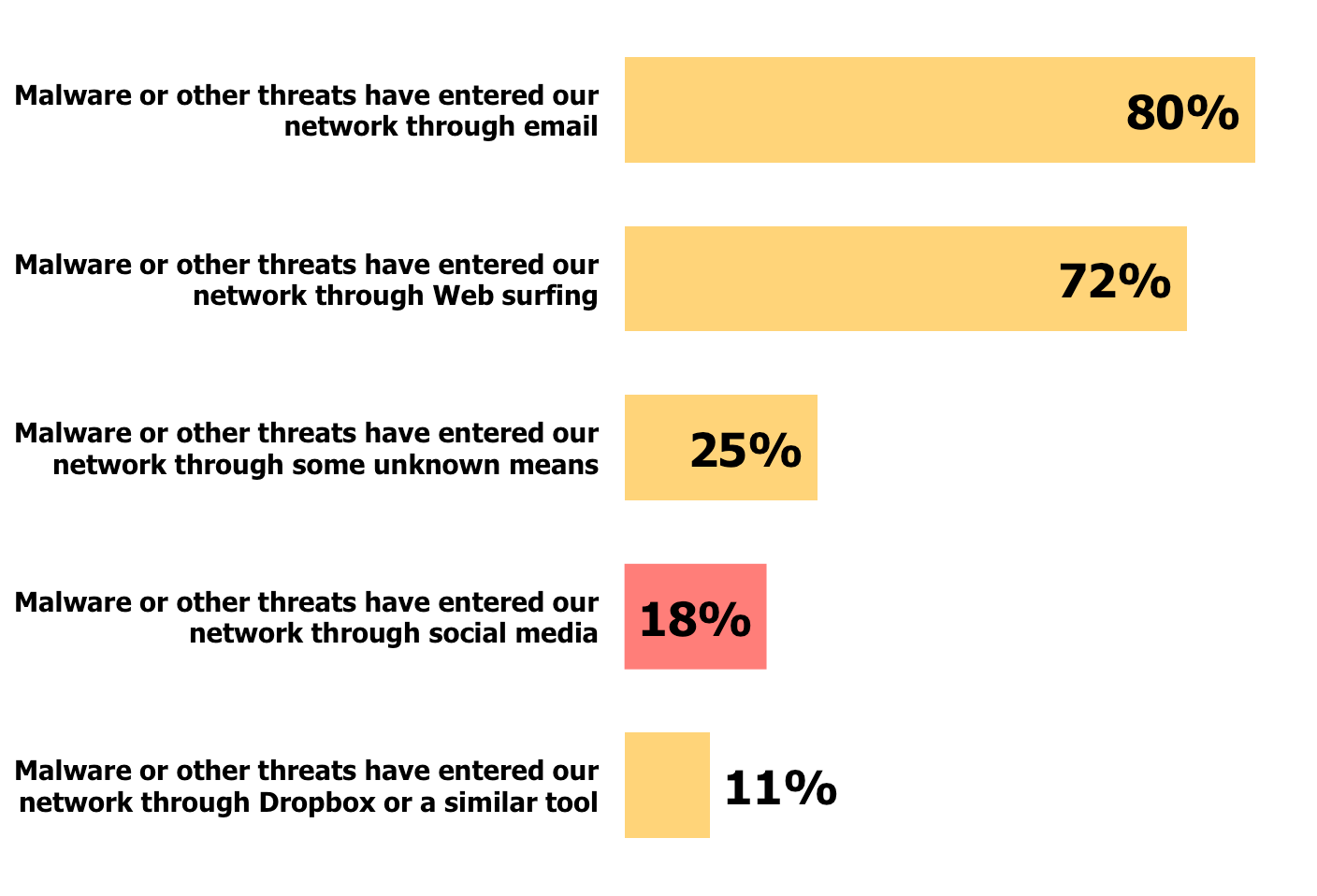
The majority of social media users have not had their accounts hacked or been the victim of malware infiltration, but this has occurred for nearly one in five organizations surveyed, as shown in Figure 5. Another one in four organizations cannot determine with any certainty the source of their malware infiltration.
Figure 5: Sources of Malware Infiltration
Social media presents a serious risk of malware infiltration and other threats in a variety of ways. For example:
- Social media platforms like Twitter that limit the number of characters necessitate the use of shortened URLs that can make it much easier for cyber criminals to disguise a link to a malicious site.
- Cybercriminals will often create bogus pages, such as a Facebook page, that will trick victims into downloading malware. Users are sometimes offered a desired capability, such as the ability to find out who visited their Facebook profile, and are willing to provide their login credentials or click on a link to obtain these “features”.
- Social media can also be the target of state-sponsored attacks. For example, in December 2015 Twitter issued a security alert to some of its users that they might have been “targeted by state-sponsored actors”, the first alert of its type made by the company.
- Moreover, malvertising is on the increase and can infect leading social media properties. A promoted Twittercard was recently discovered that can lead to installation of malware designed to steal Facebook credentials.
Compounding the problem is that many organizations have not deployed solutions specifically designed to monitor or defend against malware infiltration via social media: the survey conducted for this white paper found that 27% of organizations do not monitor social media or social network usage, and 28% have not deployed separate security solutions for social media.
This was an excerpt from Best Practices for Social Media Archiving and Security from Osterman Research. The full report is available for download here.
Latest posts by Smarsh (see all)
- Strategic Partnerships Highlighted at SmarshCONNECT 2024 - April 15, 2024
- What Are Financial Firms Saying About 2023’s Regulatory Squeeze? - January 10, 2024
- Form ADV Amendments: Frequently Asked Questions (FAQ) for RIAs - December 6, 2023