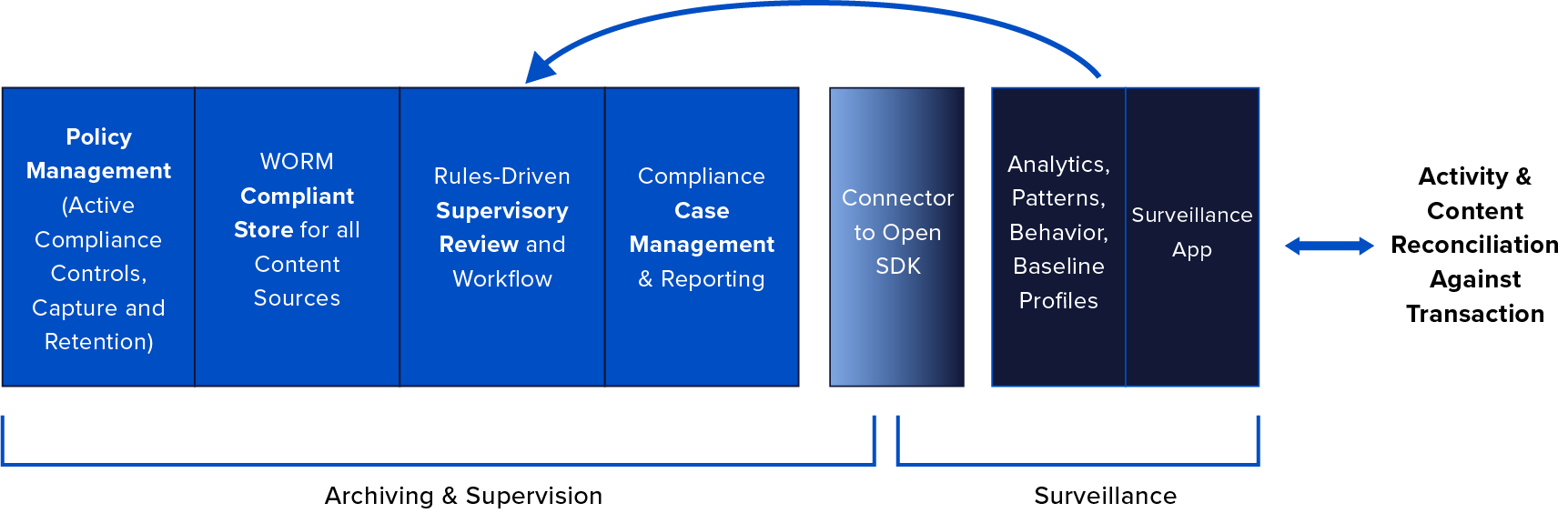
As follow up on the earlier post that described the collision of supervision and surveillance as ‘Superveillance,’ we want to dive deeper into key principles and attributes that firms should consider as they seek solutions that go beyond the boundaries of traditional supervisory and surveillance tools.
As a starting point, we’d like to suggest a common definition that would uniquely describe it as a solution to address today’s communication patterns and information risks. This definition must recognize that a variety of market disciplines are converging upon a holistic view of information risks (as discussed in a recent blog and report located here). These disciplines include:
- Technologies to manage employee communications (e.g. messaging, archiving, unified communications, etc.);
- Voice, video and other rich media-centric technologies (e.g. PBX and VOIP-enabled communications, voice recorders and transcription, etc.);
- AI, machine learning, behavioral and sentiment analysis technologies; and
- Products designed to manage structured data and transactional activity
Each of these areas of technology provides an important component to meeting broad regulatory mandates such as MiFID II that requires that all communications leading to a transaction be captured and reconciled. However, in order to address each of the elements discussed in the previous post, we’d like to offer the following as a definition for Superveillance to address these requirements:
Superveillance = Holistic insight into conduct across activities and communications channels, using a continuous feedback loop of pre-defined rules (Supervision) and identification of anomalous behavior (Surveillance).
Superveillance can be expressed visually as delivering capabilities that cover the spectrum – from the known, regulatory-driven supervisory requirements to the unknown and hidden risks that are uncovered through the use of advanced analytics. It encompasses the compliance fundamentals of policy management and storage, to the ability to use behavioral and sentiment analysis to uncover actions of high-risk brokers requiring heightened supervision. Very importantly, the outcomes in uncovering unknown risks should be fed back to build into new policies and rules for use in future supervisory tasks. Superveillance should also treat each content source natively, so the breadth of email, social media, unified communications and other sources can be normalized and delivered to external systems for trade reconciliation.
Defining the Ideal Superveillance Solution Attributes
Given the number of specialized technology domains touched by superveillance, don’t expect a ‘one-size-fits-all’ solution. Many firms have already invested in specific components, and are more concerned about how new technologies will interoperate or feed those existing solutions. Superveillance should be a critical element of the risk management fabric within an organization and, accordingly, firms should be prioritizing the following attributes when evaluating solutions or writing RFPs:
- Openness and extensibility: Superveillance requires the ability to deliver content downstream, and return insights back upstream to further inform policies. Doing so requires fully accessible APIs, connectors, and SDKs to address custom content sources. The benefits of leveraging cloud technologies are greatly diminished if utilizing technology that cannot communicate or collaborate with other vital systems
- Ability to preserve all content sources: firms today are using a multitude of communications sources, each of which must be captured and preserved to meet regulatory mandates. Modern superveillance solutions will handle each of those sources natively, with conversations preserved for more efficient review and analysis – unlike legacy supervisory tools that convert non-email sources into an email format
- Coverage for the Compliance Fundamentals: Solutions touching superveillance processes must be purpose-built for compliance and ensure that content is captured with the appropriate chain-of-custody, immutable storage, and policy management capabilities required by any SEC, FINRA, or MiFID II regulated firm. Superveillance should be thought of as extending the boundaries of traditional supervisory review – it does not replace or diminish the importance of managing the day-to-day tasks more efficiently or effectively.
- Scale and performance: Give the large volume of transactions requiring reconciliation, as well as the overwhelming volume of communications data in general, superveillance solutions must be designed for enterprise-scale, and not restricting the use of analytics to defined sub-sets of data applying only to registered representatives. Today’s information risks can reside anywhere, and having the ability to broaden the supervisory lens to cover all corners and edges of the risk perimeter is paramount
- Security and Privacy by Design: clearly, superveillance solutions will touch some of the most sensitive and important assets governed by a firm. Any solution designed for use in today’s world of increasingly complex security threats and evolving data privacy mandates must provide the audited protocols, third-party attestations, and accompany in-house expertise to reveal and respond to any risk that is exposed in its everyday use. As we see across the industry – compliance must work in harmony with other functions to create a more effective response to today’s information risks.
Where to Go from Here
Given the significant differences between traditional supervisory and surveillance tools, a good place to start is to check your vocabulary and definitions to make sure you are speaking the same language as your vendor. Once the proper nomenclature is established, firms should explore whether those traditional capabilities are equipped to address their current communications patterns and today’s information risks – or whether defining the requirements for a Superveillance solution is the better path toward a holistic approach to achieving insights across activities and communications networks.
Contributors to this post include: Robert Cruz, Gregory Breeze and Shaun Hurst
Latest posts by Robert Cruz (see all)
- The Big Question at SIFMA C&L Orlando: “Can We Just Be Done with Off-Channel Enforcement Now?” - March 25, 2024
- Off-Channel Enforcement Update: The Value of Self-Reporting Becomes Clearer - February 15, 2024
- FINRA 2024 Annual Regulatory Oversight Report: Impact on Digital Communications Practices - January 11, 2024