Examination Priorities: Regulators Focus on Cybersecurity and Technology Governance in 2020
Year after year, we have seen FINRA’s focus and reliance on technology in its examination process continue to grow. It isn’t only increasingly using algorithms and computer technology to guide its staff. In its 2020 Risk Monitoring and Exam Priorities Letter, FINRA made it clear, given member firms’ increased reliance on technology, that firms should expect to see it focusing on change and problem management practices and other technology governance issues. Similarly, the SEC recently announced that its Office of Compliance Inspections and Examination (“OCIE”) will continue to prioritize information security in each of its five examination programs during 2020.
As the industry relies more and more on technology systems, examiners’ questions are focusing on such things as proper configuration of network storage devices, information security governance programs, and retail trading information security. In the past 12 months we have seen cybersecurity and technology governance questions predominate information requests. Many of these questions can leave even the most technologically savvy firms scratching their heads. The difficulty of answering these detailed requests can be mitigated with an understanding of the questions member firms are being asked, and an internal risk assessment. The assessment should determine what systems your firm is using, how they are being used, who has control over those systems and what information is being stored in each system.
Safeguarding customer information and firm business records
FINRA tells us that the primary federal securities laws governing a firm’s cybersecurity program is SEC Rule 30 of Regulation S-P, which requires written policies and procedures to address the safeguarding of customer information and firm business records. It is a member firm’s responsibility to understand and follow Rule 30 and all other cybersecurity statutes, including those implemented at the Self-Regulatory Organization (SRO) level. Broker-dealers and investment advisors alike should establish a point person for their technology and cybersecurity program that can manage extended deadlines with complex requirements.
Point person aside, the responsibility to maintain compliance with SEC Rule 30 and SEC Rule 17a-4 trickles down to every employee of the broker-dealer and the investment advisor. Every employee in a firm that has an email address may be subject to phishing email attacks, regardless of their role or authority. Employees that handle a firm’s monetary systems must be aware that ransomware attacks, identity theft, and fraudulent third-party wire requests have been on the rise. In keeping with FINRA and SEC Rules, a firm’s principals are responsible for implementing such policies together with cybersecurity training programs that can reasonably prevent their employees from falling prey to such breaches.
Risk assessments and cybersecurity at scale
FINRA member firms, as well as registered investment advisors, must establish effective cybersecurity programs that utilize risk-based management in their processes. Effective programs use regular risk assessments with scheduled follow-ups, and vulnerability and penetration testing coupled with role-specific training programs and exercises. FINRA published a tool for small firm members to use to conduct a cybersecurity risk assessment. The tool can easily be used by investment advisors as a guide when conducting their own cybersecurity risk assessment.
FINRA member firms (as well as investment advisors) with branch offices and/or independent rep platforms should also implement these tools as part of their “branch office” inspection programs. Broker-dealers and investment advisors with sophisticated cybersecurity programs have successfully implemented system usage behavior analytics and data loss prevention tools, along with security information and event management mechanisms. FINRA, and to a certain extent the SEC, does acknowledge that the level of cybersecurity efforts can be tailored to the size and scope of each member firm. They also acknowledge that some of the more sophisticated cybersecurity methods cannot be required of all firms. However, the rules apply to small firms as well as large firms. As such, all broker-dealers and investment advisors should strive to implement a program that exceeds at least the minimum requirements in order to avoid unnecessary regulatory attention.
New FINRA examination questions
In the first couple weeks of 2020, FINRA member firms are being notified of their new points of contact and their assigned business grouping and subgrouping. As part of this program, member firms may inquire as to what their new exam cycle will be so that they can be better prepared. That said, if your firm has not been examined in the past three years, you may be surprised to see how many questions touch on your cybersecurity and technology governance processes and procedures. Similarly, investment advisors who have not been examined by the SEC or state authorities should expect to see questions related to how firms not only protect their clients’ personal financial information, but also focus on:
- governance and risk management
- access controls
- data loss prevention
- vendor management
- training
- incident response and resiliency
In particular, firms may be asked questions such as:
- If there have been material changes in your firm’s business operations, what modifications, if any have been made to your firm’s Business Continuity Plan?
- Does your firm have a formal “onboarding” and “offboarding” process/procedure which must be followed to grant and/or terminate an employee’s access to your systems? How does your firm determine which employees have access to what information and/or what systems? How are your processes relative to who is authorized to grant access (or remove access) to your system and how are such requests documented and approved?
- What are your firm’s procedures for tracking information technology problems and their remediation? Does your firm categorize problems based on their business impact?
- What controls does your firm have to mitigate system capacity performance and integrity issues that may undermine its ability to conduct its business?
- Does your firm operate in a BYOD environment or does your firm provide hardware to its employees (phones, tablets, computers, etc.)? If your firm operates in a BYOD environment, how does it make sure the hardware its staff is using has appropriate protection installed and maintained?
- What controls does your firm have around the proper disposal of retired hardware that may contain client confidential information and potential network information that could create an intrusion vulnerability?
More focus on access management
Examinations can also include scrutiny of a firm’s control over access management. This includes the termination of former employees’ site and storage access, implementation of procedures to log, monitor, and supervise employees’ cyber activity, and the geographic limitation of user access. As firms are reviewing their compliance programs and their written compliance and supervisory procedures, they should take their firm’s structure and demographics into consideration and carefully review all cyber-related policies to make sure they adequately address how their firm transacts business. Often firms are cited by both the SEC and FINRA for having “off the shelf” procedures which are too generic and/or do not accurately reflect the way their firm actually conducts business.
FINRA has also dinged member firms for their failure to establish formal processes to conduct ongoing risk assessments of their data, systems, and applications. Again, this is a relatively “simple” process using FINRA’s Small Firm Cybersecurity Checklist. It can be time-consuming and the process should involve multiple people from each area and level of the firm’s business. Including different people from each area of your firm’s business, as well as individuals from each level within your firm, will likely surface some interesting considerations. You are likely to discover that individuals, based on their age group and backgrounds, communicate very differently within your firm than your firm’s management team communicates. Microsoft recently conducted a survey that illustrates the mix of communication channels used by different age segments of the workforce:
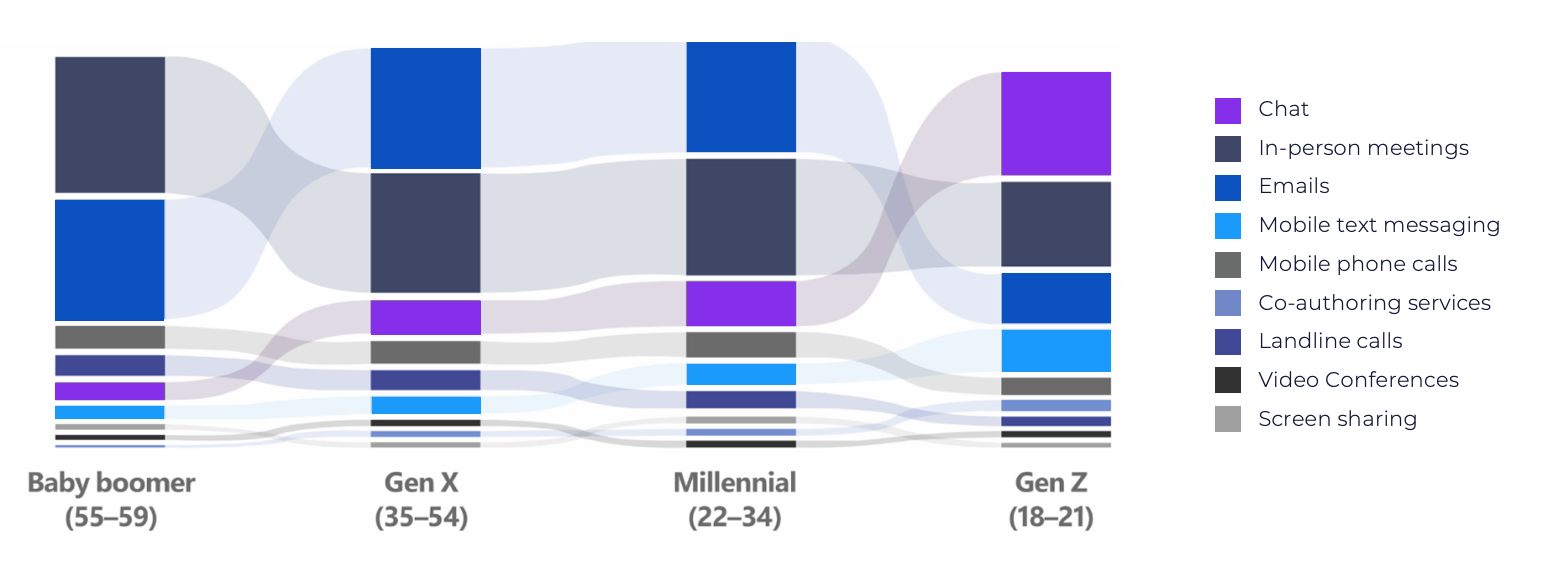
Image: Microsoft blog, "New survey explores the changing landscape of teamwork"
Firms need to account for how their employees use technology to conduct business, which in turn creates regulatory risk and business risk for the firm. Firms with branch offices should also be aware of the challenges these offices create and the heightened scrutiny these locations can receive during an examination. Branch offices often suffer from program gaps as simple as weak passwords, unauthorized file storage locations, unauthorized CRM systems, unauthorized collaborative platforms, untimely patching of cyber-deficiencies and updating of software, lack of control over removable storage devices, and failures to properly encrypt data and report cyber-events.
SEC Rule 17a-4 specifies minimum requirements for the electronic storage of broker-dealer records, particularly the storage format and the amount of time the records must be held. Similarly, SEC Rules 204-2 specifies the requirements for investment advisors. The records that broker-dealers are mandated to maintain must be stored in non-rewriteable and non-erasable format, commonly referred to as “WORM” format or “Write Once Read Many.” Such records may not be preserved in a format that allows for any alterations during the retention period. These records are to be indexed and available for a period of six years. For the first two years, they must be immediately accessible. Fortunately for some broker-dealers, SEC Rule 17a-4 does allow for a degree of outsourcing of these duties to a designated third party. This designated third party helps the broker-dealer with the production of its 17a-4 records upon regulatory request. Ultimately, no matter the level of delegation, FINRA member firms remain responsible to vigilantly ensure that cyber policies and systems are properly maintained.
Filing Electronic Storage Notice with FINRA
FINRA member firms that elect to store records electronically are required to file “17a-4; Electronic Records Storage Notice” with FINRA. They must also obtain evidence from their vendor that such records are maintained in compliance with SEC Rule 17a-4, commonly referred to as a 17a-4 letter. Member firms who utilize online vendors to store records should make sure that they have filed a 17a-4; Electronic Storage Notice with FINRA, and that they have obtained 17a-4 letters from their vendors storing books and records required by SEC Rule 17a-3. Regulated firms can easily leverage their vendor partnership to make sure that the information they are maintaining electronically are stored in compliance with Rule 17a-4 or Rule 204-2.
Start preparing now for your next FINRA exam, paying particular attention to your cybersecurity and technology governance processes and procedures. This will help you the next time FINRA examiners conduct your cycle examination. You should be prepared to answer tough questions about where your data is maintained and how it is being stored, and be able to quickly produce those records for examination. FINRA’s (and the SEC’s) increasing focus on cybersecurity and technology during its member examinations should not surprise any regulated firm.
The ability to demonstrate the implementation and existence of your cybersecurity program, and its compliance with the relevant cyber statutes and guidance, are absolute examination requirements for all firms. Firms that can prove they frequently utilize cyber-compliance tools find that their business recovers quicker from cyber-events and have easier FINRA cycle examinations. These firms have a solid understanding of minimum requirements of SEC Rule 17a-4 and SEC Rule 30, and strive to exceed those minimums. The next time you’re asked a cybersecurity question, from a client or examiner, you will know the answer and have the records to show it.

Professional Archive
Retain critical information in a single, secure, search-ready repository where it can be actively monitored and produced on-demand.
Smarsh Blog
Our internal subject matter experts and our network of external industry experts are featured with insights into the technology and industry trends that affect your electronic communications compliance initiatives. Sign up to benefit from their deep understanding, tips and best practices regarding how your company can manage compliance risk while unlocking the business value of your communications data.




Subscribe to the Smarsh Blog Digest
Subscribe to receive a monthly digest of articles exploring regulatory updates, news, trends and best practices in electronic communications capture and archiving.
Smarsh handles information you submit to Smarsh in accordance with its Privacy Policy. By clicking "submit", you consent to Smarsh processing your information and storing it in accordance with the Privacy Policy and agree to receive communications from Smarsh and its third-party partners regarding products and services that may be of interest to you. You may withdraw your consent at any time by emailing privacy@smarsh.com.
FOLLOW US