Vendor Tiering: Essential Guide for Risk Management
Navigating the complexities of vendor relationships necessitates a strategic approach, underscored by the adoption of vendor tiering as a core component of risk management.
A mere 34% of enterprises maintain a comprehensive vendor ledger—a shortfall often attributed to the absence of centralized control. In the realm of risk and compliance, where oversights have led to substantial financial losses, the critical role of vendor tiering in ensuring operational resilience and regulatory compliance becomes indisputably clear.
The Essential Role of Vendor Tiering in Risk Management
The need for vendor tiering becomes particularly evident when considering the array of risks associated with vendors. Nearly 40% of businesses neglect regular risk assessments, exposing themselves to a spectrum and compliance breaches.
In contrast, those who leverage a thorough vendor criticality matrix, assess and rank vendors annually, undeniably strengthen their competitive edge.
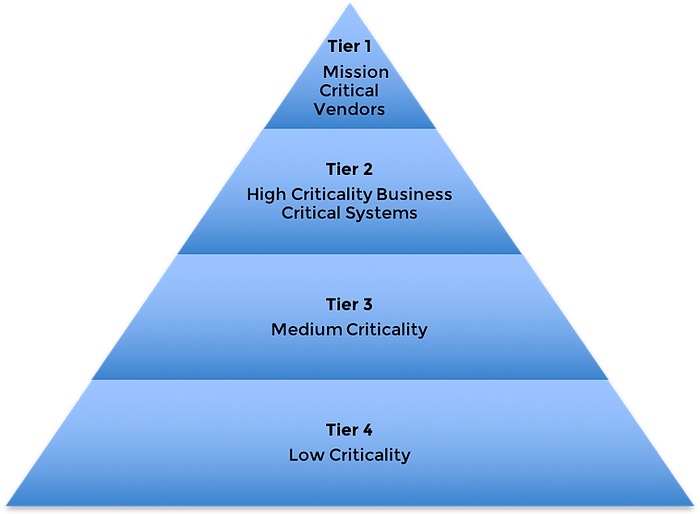
Understanding the 4-Tier Vendor Classification System
Smarsh has a 4-tier classification system based on data access, network or physical access and business criticality.
Tier 1 Vendor: Core Operational Vendors
These vendors are pivotal to the business's core operations, warranting a comprehensive assessment reflective of their high-risk potential and critical operational role.
Tier 2 Vendor: Significant Risk Vendors
While still representing significant risk, Tier 2 vendors warrant a detailed but less intensive evaluation focused on their security policies and infrastructural safeguards.
Tier 3 Vendor: Medium Risk Category
Occupying the medium risk group, vendors in this category need tailored assessments to identify and mitigate specific types of vendor risk.
Tier 4 Vendor: Optional Low-Risk Category
An optional classification for those vendors whose risk profile is minimal, such as those without sensitive data access.
Strategically Categorizing Vendors: Beyond One-Size-Fits-All
Effective vendor tiering mandates a departure from blanket categorizations, steering towards a nuanced understanding of service and access levels. For larger organizations, this means grouping vendors by service types followed by an access-centric subcategorization. Smaller enterprises might start with access as the primary differentiator. This granularity facilitates a focused assessment of vendor criticality, probing the extent, nature, and frequency of data access, as well as the vendor's systemic importance.
Evaluating Vendor Criticality and Security: A Dual Assessment Approach
This dual assessment—of criticality and security—yields a weighted risk profile for each vendor, enabling businesses to calibrate their risk management strategies according to an objective, data-supported vendor risk and control matrix. The alignment of this assessment with established benchmarks for acceptable risk epitomizes a disciplined approach to vendor management.
Leveraging Vendor Tiering for Operational Resilience and Compliance
Vendor tiering, therefore, is not merely a compliance checklist item; it is a strategic framework integral to a business's risk management fortitude. Embracing this approach ensures a defensible posture against the vicissitudes of vendor-associated risks and regulatory demands. Businesses intent on mastering vendor tiering, and by extension their risk management processes, are encouraged to engage with platforms such as Smarsh. Such collaboration represents a proactive step towards centralizing control, optimizing the vendor criticality matrix, and safeguarding the business ecosystem from the inherent risks of vendor partnerships.
Share this post!
Smarsh Blog
Our internal subject matter experts and our network of external industry experts are featured with insights into the technology and industry trends that affect your electronic communications compliance initiatives. Sign up to benefit from their deep understanding, tips and best practices regarding how your company can manage compliance risk while unlocking the business value of your communications data.
Ready to enable compliant productivity?
Join the 6,500+ customers using Smarsh to drive their business forward.





Subscribe to the Smarsh Blog Digest
Subscribe to receive a monthly digest of articles exploring regulatory updates, news, trends and best practices in electronic communications capture and archiving.
Smarsh handles information you submit to Smarsh in accordance with its Privacy Policy. By clicking "submit", you consent to Smarsh processing your information and storing it in accordance with the Privacy Policy and agree to receive communications from Smarsh and its third-party partners regarding products and services that may be of interest to you. You may withdraw your consent at any time by emailing [email protected].
FOLLOW US